- Регистрация
- 17 Февраль 2018
- Сообщения
- 40 830
- Лучшие ответы
- 0
- Реакции
- 0
- Баллы
- 8 093
Offline
Abusing Microsoft’s reputation may make scam harder to spot.

Credit: Getty Images
There are reports that a legitimate Microsoft email address—which Microsoft explicitly says customers should add to their allow list—is delivering scam spam.
The emails originate from no-reply-powerbi@microsoft.com, an address tied to Power BI. The Microsoft platform provides analytics and business intelligence from various sources that can be integrated into a single dashboard. Microsoft documentation says that the address is used to send subscription emails to mail-enabled security groups. To prevent spam filters from blocking the address, the company advises users to add it to allow lists.
From Microsoft, with malice
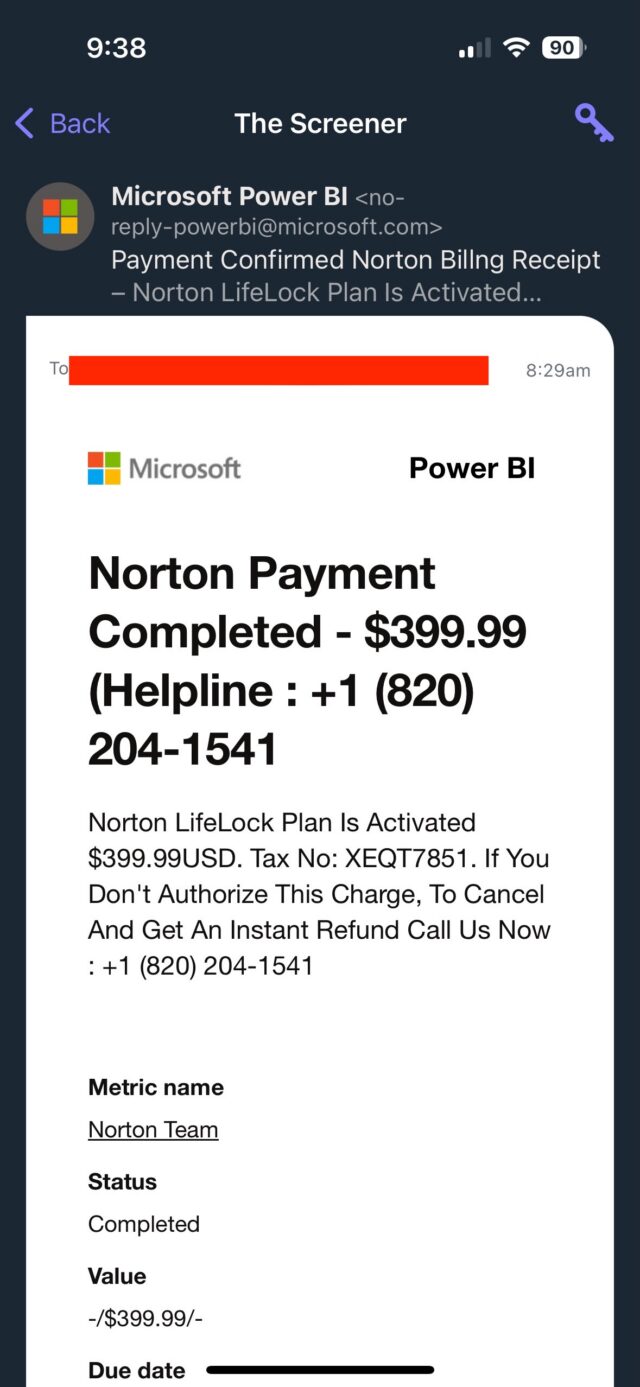
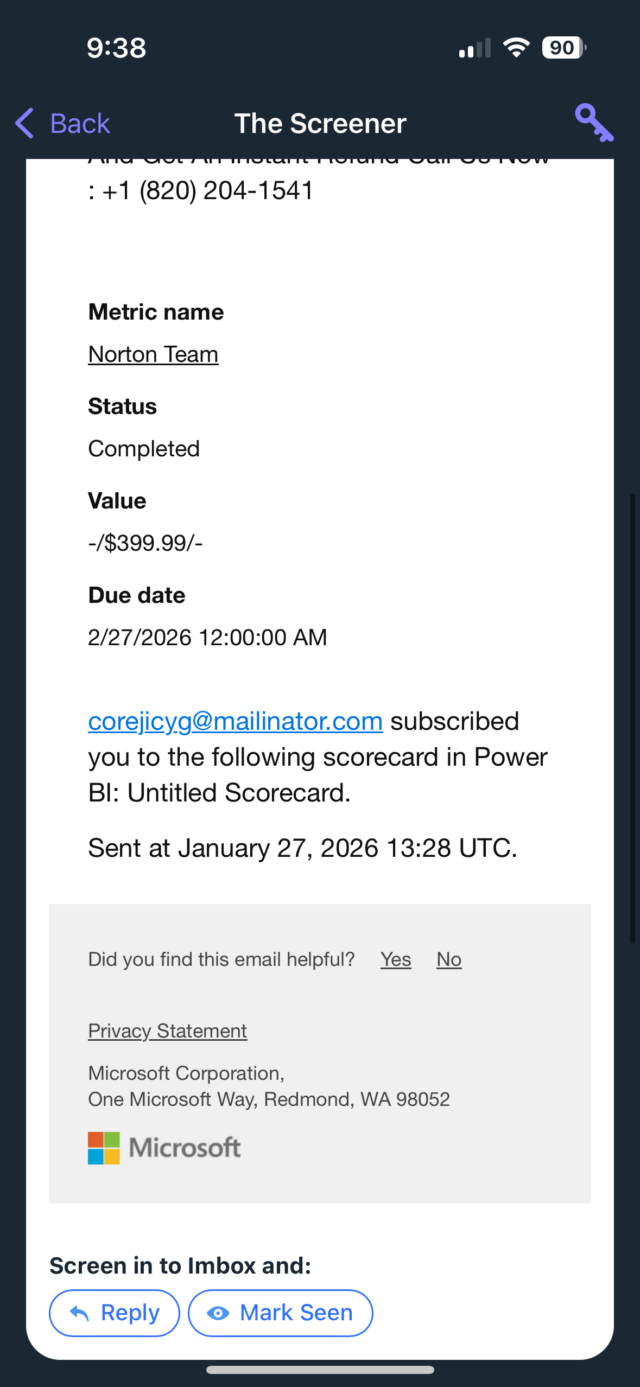
According to an Ars reader, the address on Tuesday sent her an email claiming (falsely) that a $399 charge had been made to her. It provided a phone number to call to dispute the transaction. A man who answered a call asking to cancel the sale directed me to download and install a remote access application, presumably so he could then take control of my Mac or Windows machine (Linux wasn’t allowed). The email, captured in the two screenshots below, looked like this:
Online searches returned a dozen or so accounts of other people reporting receiving the same email. Some of the spam was reported on Microsoft’s own website.
Sarah Sabotka, a threat researcher at security firm Proofpoint, said the scammers are abusing a Power Bi function that allows external email addresses to be added as subscribers for the Power Bi reports. The mention of the subscription is buried at the very bottom of the message, where it’s easy to miss. The researcher explained:
The abuse of a legitimate service, like Microsoft Power BI, adds an additional layer of credibility to the social engineering. The actual scam occurs during the voice interaction, which helps attackers evade traditional email-based detection and security controls. Further, attackers gain two advantages at once: the email is sent from a trusted Microsoft domain, and the lack of malicious links or attachments reduces the likelihood of automated filtering. While the emails originate from Microsoft infrastructure, the content and intent are fully controlled by the attacker via misuse of a legitimate feature.
Scammers have abused Microsoft Power Bi functionality in the past. Security firm Cofense reported in September that it found a spam campaign that transmitted phishing links that were hosted on the platform. Companies besides Microsoft that have experienced similar abuse include Google, according to Check Point. The security firm found a run of nearly 9,400 emails that were sent through the Google Cloud Application Integration platform.
A key detail that’s currently unknown is: Do users have to explicitly opt in to receiving emails from email addresses like no-reply-powerbi@microsoft.com, and can scammers send them to any external address automatically? A Microsoft representative said he’s looking into reports and didn’t have information immediately available. For more experienced Internet users, scams like this one are easy to spot. For others, scams that originate from a known sender with a clean reputation are more believable.
e
elellel
Thanks, Dan, for thoroughly and quickly reporting this!
January 28, 2026 at 12:15 am


Credit: Getty Images
There are reports that a legitimate Microsoft email address—which Microsoft explicitly says customers should add to their allow list—is delivering scam spam.
The emails originate from no-reply-powerbi@microsoft.com, an address tied to Power BI. The Microsoft platform provides analytics and business intelligence from various sources that can be integrated into a single dashboard. Microsoft documentation says that the address is used to send subscription emails to mail-enabled security groups. To prevent spam filters from blocking the address, the company advises users to add it to allow lists.
From Microsoft, with malice
According to an Ars reader, the address on Tuesday sent her an email claiming (falsely) that a $399 charge had been made to her. It provided a phone number to call to dispute the transaction. A man who answered a call asking to cancel the sale directed me to download and install a remote access application, presumably so he could then take control of my Mac or Windows machine (Linux wasn’t allowed). The email, captured in the two screenshots below, looked like this:


Online searches returned a dozen or so accounts of other people reporting receiving the same email. Some of the spam was reported on Microsoft’s own website.
Sarah Sabotka, a threat researcher at security firm Proofpoint, said the scammers are abusing a Power Bi function that allows external email addresses to be added as subscribers for the Power Bi reports. The mention of the subscription is buried at the very bottom of the message, where it’s easy to miss. The researcher explained:
The abuse of a legitimate service, like Microsoft Power BI, adds an additional layer of credibility to the social engineering. The actual scam occurs during the voice interaction, which helps attackers evade traditional email-based detection and security controls. Further, attackers gain two advantages at once: the email is sent from a trusted Microsoft domain, and the lack of malicious links or attachments reduces the likelihood of automated filtering. While the emails originate from Microsoft infrastructure, the content and intent are fully controlled by the attacker via misuse of a legitimate feature.
Scammers have abused Microsoft Power Bi functionality in the past. Security firm Cofense reported in September that it found a spam campaign that transmitted phishing links that were hosted on the platform. Companies besides Microsoft that have experienced similar abuse include Google, according to Check Point. The security firm found a run of nearly 9,400 emails that were sent through the Google Cloud Application Integration platform.
A key detail that’s currently unknown is: Do users have to explicitly opt in to receiving emails from email addresses like no-reply-powerbi@microsoft.com, and can scammers send them to any external address automatically? A Microsoft representative said he’s looking into reports and didn’t have information immediately available. For more experienced Internet users, scams like this one are easy to spot. For others, scams that originate from a known sender with a clean reputation are more believable.
e
elellel
I'll be that guy: the errors in this message scream that this is a scam.
Billing in the subject is misspelled.
The message is from Microsoft about a Norton subscription.
The grammar is atrocious - let's capitalize each word!
Subscribed by a user/email with zero connection to Microsoft or Norton.
Does this even have a certificate from Microsoft?
As the person who sent in this tip to begin with, my real concern is the existence of the attack vector, rather than the particular scam. If this scam operation has the ability to send social engineering scams literally from Microsoft’s domain without spoofing it, that’s pretty concerning regardless of how amateurish a particular attack may be/appear.Billing in the subject is misspelled.
The message is from Microsoft about a Norton subscription.
The grammar is atrocious - let's capitalize each word!
Subscribed by a user/email with zero connection to Microsoft or Norton.
Does this even have a certificate from Microsoft?
Thanks, Dan, for thoroughly and quickly reporting this!
January 28, 2026 at 12:15 am
