- Регистрация
- 17 Февраль 2018
- Сообщения
- 40 830
- Лучшие ответы
- 0
- Реакции
- 0
- Баллы
- 8 093
Offline
Company’s autodiscover caused users’ test credentials to be sent outside Microsoft networks.


Credit: Getty Images
From the Department of Bizarre Anomalies: Microsoft has suppressed an unexplained anomaly on its network that was routing traffic destined to example.com—a domain reserved for testing purposes—to a maker of electronics cables located in Japan.
Under the RFC2606—an official standard maintained by the Internet Engineering Task Force—example.com isn’t obtainable by any party. Instead it resolves to IP addresses assigned to Internet Assiged Names Authority. The designation is intended to prevent third parties from being bombarded with traffic when developers, penetration testers, and others need a domain for testing or discussing technical issues. Instead of naming an Internet-routable domain, they are to choose example.com or two others, example.net and example.org.
Misconfig gone, but is it fixed?
Output from the terminal command cURL shows that devices inside Azure and other Microsoft networks have been routing some traffic to subdomains of sei.co.jp, a domain belonging to Sumitomo Electric. Most of the resulting text is exactly what’s expected. The exception is the JSON-based response. Here’s the JSON output from Friday:
{"email":"email@example.com","services":[],"protocols":[{"protocol":"imap","hostname":"imapgms.jnet.sei.co.jp","port":993,"encryption":"ssl","username":"email@example.com","validated":false},{"protocol":"smtp","hostname":"smtpgms.jnet.sei.co.jp","port":465,"encryption":"ssl","username":"email@example.com","validated":false}]}
Similarly, results when adding a new account for test@example.com in Outlook looked like this:
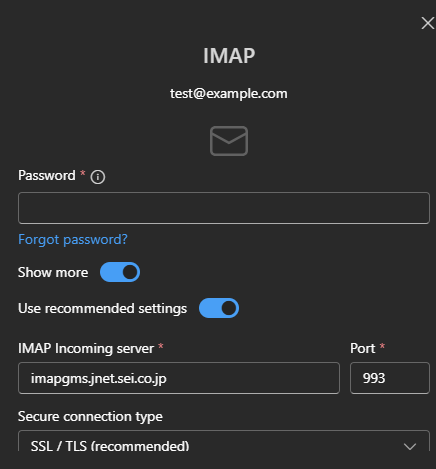
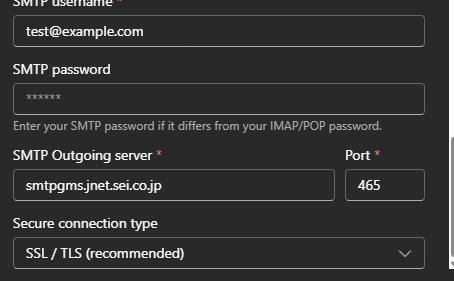
In both cases, the results show that Microsoft was routing email traffic to two sei.co.jp subdomains: imapgms.jnet.sei.co.jp and smtpgms.jnet.sei.co.jp. The behavior was the result of Microsoft’s autodiscover service.
“I’m admittedly not an expert in Microsoft’s internal workings, but this appears to be a simple misconfiguration,” Michael Taggart, a senior cybersecurity researcher at UCLA Health, said. “The result is that anyone who tries to set up an Outlook account on an example.com domain might accidentally send test credentials to those sei.co.jp subdomains.”
When asked early Friday afternoon why Microsoft was doing this, a representative had no answer and asked for more time. By Monday morning, the improper routing was no longer occurring, but the representative still had no answer.
Update: in an email sent after this post went live, the representative confirmed that Microsoft has “updated the service to no longer provide suggested server information for example.com.” As already reported here, the behavior only affected people configuring email accounts through the Outlook autoconfiguration feature. The representative added that Microsoft is investigating.
The new JSON response suggested that, as of Monday morning, Microsoft hadn’t fixed the endpoint routing traffic to the Sumitomo Electric servers. Instead, the JSON response no longer occurs. Where the output was occurring on Friday, the command now simply sits and hangs for 10 or 20 seconds and then terminates with a not found error. This behavior can be seen in the following output:
> GET /autodetect/detect?app=outlookdesktopBasic HTTP/2
> Host: prod.autodetect.outlook.cloud.microsoft
> Authorization: Basic ZW1haWxAZXhhbXBsZS5jb206cGFzc3dvcmQ=
> User-Agent: curl/8.14.1
> Accept: */*
>
* Request completely sent off
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
< HTTP/2 204
< date: Mon, 26 Jan 2026 18:23:55 GMT
< server: Kestrel
< strict-transport-security: max-age=2592000
< x-olm-source-endpoint: /detect
< x-provider-id: Unknown
< x-debug-support: eyJkZWNpc2lvbiI6ImF1dG9EdjIgPiBhdXRvRHYxID4gZml4ZWQgZGIgcHJvdmlkZXIgPiBmaXhlZCBkYiBkb21haW4gcHJvdG9jb2xzID4gZGIgcHJvdmlkZXIgPiBkYiBkb21haW4gcHJvdG9jb2xzIiwiYXV0b0QiOnsidjIiOm51bGwsInYxIjpudWxsfSwiZGIiOnsicHJvdmlkZXIiOm51bGwsImRvbWFpbiI6eyJmaXhlZCI6ZmFsc2UsImF1dG9EdjJFbmRwb2ludCI6bnVsbCwicHJvdmlkZXJJZCI6bnVsbCwicHJvdG9jb2xzIjpudWxsfX19
< x-autodv2-error: ENOTFOUND
“It looks like they may have outright removed the endpoint that validates the email, because I’m seeing ‘not found’ errors,” said Dan Tentler, founder of Phobos Group. As denoted by ENOTFOUND, the error “suggests that [Microsoft admins] just ripped out whatever this thing was.”
It’s unclear how Sumitomo Electric’s domain would have found itself part of this mess. Microsoft last year said the Japanese company’s parent company, Sumitomo Corp., was deploying Microsoft 365 Copilot, but that still doesn’t explain why a subsidiary’s domain was added to Microsoft’s network configuration.
Questions sent to Microsoft include: How are autodiscover records added at Microsoft; was the routing intentional; and how long has the behavior been occurring? (Tinyapps.org, which noted the odd routing behavior earlier this month, said it lasted five years.) There doesn’t appear to be anything nefarious about the improper routing, and as long as people inside Microsoft’s network weren’t sending live credentials in tests, there was no danger posed.
There’s still reason for concern. In 2024, Microsoft revealed that one of its admins had assigned administrative privileges to a test account on the company network and then forgot about it. Russia-state hackers seized on the gaffe to gain initial access to Microsoft’s system. They went on to root through the network and monitor top executives’ email for two months. The routing misconfiguration for example.com raises the question: What other possibly more severe errors lurk on the network?

J.King
January 26, 2026 at 10:45 pm


Credit: Getty Images
From the Department of Bizarre Anomalies: Microsoft has suppressed an unexplained anomaly on its network that was routing traffic destined to example.com—a domain reserved for testing purposes—to a maker of electronics cables located in Japan.
Under the RFC2606—an official standard maintained by the Internet Engineering Task Force—example.com isn’t obtainable by any party. Instead it resolves to IP addresses assigned to Internet Assiged Names Authority. The designation is intended to prevent third parties from being bombarded with traffic when developers, penetration testers, and others need a domain for testing or discussing technical issues. Instead of naming an Internet-routable domain, they are to choose example.com or two others, example.net and example.org.
Misconfig gone, but is it fixed?
Output from the terminal command cURL shows that devices inside Azure and other Microsoft networks have been routing some traffic to subdomains of sei.co.jp, a domain belonging to Sumitomo Electric. Most of the resulting text is exactly what’s expected. The exception is the JSON-based response. Here’s the JSON output from Friday:
{"email":"email@example.com","services":[],"protocols":[{"protocol":"imap","hostname":"imapgms.jnet.sei.co.jp","port":993,"encryption":"ssl","username":"email@example.com","validated":false},{"protocol":"smtp","hostname":"smtpgms.jnet.sei.co.jp","port":465,"encryption":"ssl","username":"email@example.com","validated":false}]}
Similarly, results when adding a new account for test@example.com in Outlook looked like this:


In both cases, the results show that Microsoft was routing email traffic to two sei.co.jp subdomains: imapgms.jnet.sei.co.jp and smtpgms.jnet.sei.co.jp. The behavior was the result of Microsoft’s autodiscover service.
“I’m admittedly not an expert in Microsoft’s internal workings, but this appears to be a simple misconfiguration,” Michael Taggart, a senior cybersecurity researcher at UCLA Health, said. “The result is that anyone who tries to set up an Outlook account on an example.com domain might accidentally send test credentials to those sei.co.jp subdomains.”
When asked early Friday afternoon why Microsoft was doing this, a representative had no answer and asked for more time. By Monday morning, the improper routing was no longer occurring, but the representative still had no answer.
Update: in an email sent after this post went live, the representative confirmed that Microsoft has “updated the service to no longer provide suggested server information for example.com.” As already reported here, the behavior only affected people configuring email accounts through the Outlook autoconfiguration feature. The representative added that Microsoft is investigating.
The new JSON response suggested that, as of Monday morning, Microsoft hadn’t fixed the endpoint routing traffic to the Sumitomo Electric servers. Instead, the JSON response no longer occurs. Where the output was occurring on Friday, the command now simply sits and hangs for 10 or 20 seconds and then terminates with a not found error. This behavior can be seen in the following output:
> GET /autodetect/detect?app=outlookdesktopBasic HTTP/2
> Host: prod.autodetect.outlook.cloud.microsoft
> Authorization: Basic ZW1haWxAZXhhbXBsZS5jb206cGFzc3dvcmQ=
> User-Agent: curl/8.14.1
> Accept: */*
>
* Request completely sent off
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
< HTTP/2 204
< date: Mon, 26 Jan 2026 18:23:55 GMT
< server: Kestrel
< strict-transport-security: max-age=2592000
< x-olm-source-endpoint: /detect
< x-provider-id: Unknown
< x-debug-support: eyJkZWNpc2lvbiI6ImF1dG9EdjIgPiBhdXRvRHYxID4gZml4ZWQgZGIgcHJvdmlkZXIgPiBmaXhlZCBkYiBkb21haW4gcHJvdG9jb2xzID4gZGIgcHJvdmlkZXIgPiBkYiBkb21haW4gcHJvdG9jb2xzIiwiYXV0b0QiOnsidjIiOm51bGwsInYxIjpudWxsfSwiZGIiOnsicHJvdmlkZXIiOm51bGwsImRvbWFpbiI6eyJmaXhlZCI6ZmFsc2UsImF1dG9EdjJFbmRwb2ludCI6bnVsbCwicHJvdmlkZXJJZCI6bnVsbCwicHJvdG9jb2xzIjpudWxsfX19
< x-autodv2-error: ENOTFOUND
“It looks like they may have outright removed the endpoint that validates the email, because I’m seeing ‘not found’ errors,” said Dan Tentler, founder of Phobos Group. As denoted by ENOTFOUND, the error “suggests that [Microsoft admins] just ripped out whatever this thing was.”
It’s unclear how Sumitomo Electric’s domain would have found itself part of this mess. Microsoft last year said the Japanese company’s parent company, Sumitomo Corp., was deploying Microsoft 365 Copilot, but that still doesn’t explain why a subsidiary’s domain was added to Microsoft’s network configuration.
Questions sent to Microsoft include: How are autodiscover records added at Microsoft; was the routing intentional; and how long has the behavior been occurring? (Tinyapps.org, which noted the odd routing behavior earlier this month, said it lasted five years.) There doesn’t appear to be anything nefarious about the improper routing, and as long as people inside Microsoft’s network weren’t sending live credentials in tests, there was no danger posed.
There’s still reason for concern. In 2024, Microsoft revealed that one of its admins had assigned administrative privileges to a test account on the company network and then forgot about it. Russia-state hackers seized on the gaffe to gain initial access to Microsoft’s system. They went on to root through the network and monitor top executives’ email for two months. The routing misconfiguration for example.com raises the question: What other possibly more severe errors lurk on the network?
J.King
I did not know that about example.com, very cool! I'm going to use it everywhere in my code now.
You shouldn't be using it in your code, just in documentation. Rather, if you want to have a placeholder in test cases and whatnot you should use example.test. that domain is guaranteed to remain unassigned, so you won't be accidentally sending traffic to a real domain, and you can give it a real address locally if connecting to an actual server is desired.January 26, 2026 at 10:45 pm
